Mar 08, 2023 by Mark Dingley
Cameras, sensors, printers, scanners … all these devices can be, or are already, connected to the internet and each other to make manufacturing safer, more efficient and more profitable.
The Industrial Internet of Things (IIoT) is the ability of physical devices to connect with the internet so that one device can talk to other devices and provide valuable data and insights.
It's a game-changer for manufacturers. This connectivity means you can track ingredients, packaging and finished goods faster and more effectively.
For example, using food sensors connected to the internet to monitor production times, shipping times and temperature means manufacturers can keep a constant watch on temperatures throughout the production, transportation and storage.
At the same time, analysing data from IIoT can help prevent manufacturing downtime and drive the continuous effort for more efficiencies.

Yet, we now live in a world where every connection to the internet can potentially be exploited by cybercriminals.
According to the Australian Cyber Security Centre (ACSC) annual cyber threat report, manufacturing is in the top 10 sectors accounting for approximately 75% of all cybersecurity incidents in FY2021-22.
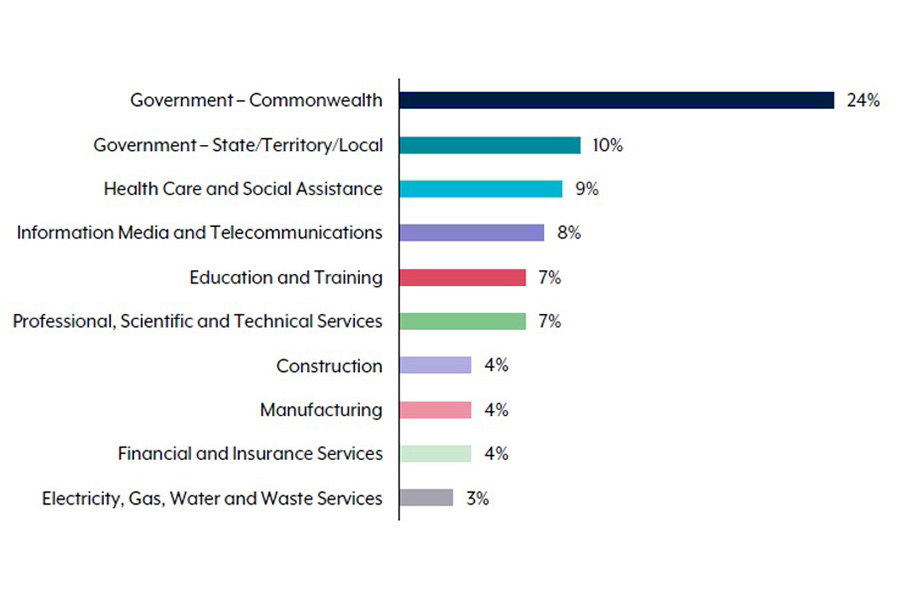
Image source: https://www.cyber.gov.au/acsc/view-all-content/reports-and-statistics/acsc-annual-cyber-threat-report-july-2021-june-2022
As a manufacturer's cloud network widens and its number of connected devices per user increases, the likelihood that it could become a cybercrime victim also rises. More connected endpoints mean there are more potential gateways for cybercriminals to gain access to networks and infrastructure systems.
Because IIoT is still emerging, conventional security approaches quickly become outdated and increasingly inadequate. There are few security standards to which organisations are held.
On top of this, criminals know that IIoT security is not mature, which makes devices an easy target. According to IoT-based attacks statistics from 2019, the average IoT device gets attacked just five minutes after it goes live.
One of the most significant risks is a distributed denial-of-service (DDoS) attack, a malicious attempt to disrupt the regular traffic of a targeted server, service or network by overwhelming the target or surrounding infrastructure with a flood of internet traffic.
In 2022, 1.3 million DDoS attacks targeted organisations in the Asia-Pacific region. That's around 8,600 DDoS attacks daily, with a new attack every 10 seconds.
Exploited machines can include computers and other networked resources, including IoT devices. Since these networks are connected to machines and entire production lines, cyberattacks can cause severe issues for manufacturers.
In fact, the operations of 43% of those hit with a cyberattack were affected for two days, with a further 19% saying the impact lasted for three or more days.
However, the whole point of IIoT is to benefit from the connectivity of devices. So how do you reap the rewards without putting your manufacturing business at risk?
There are seven key things that manufacturers can do to improve their cybersecurity and tap into the advantages of IIoT:
It is important to actively inventory and track all devices on the network and to detect unauthorised devices. That’s because unauthorised devices can be attacked and used to orchestrate cyberattacks on equipment and other systems.
Also, track all software running on the network to detect outdated versions and remove unauthorised ones. Even the security basics, such as changing default login credentials and applying patches (security updates) as and when they're released, can go a long way to help secure IIoT devices.

Every connection to the internet gives cybercriminals a potential gateway to attack. So, look at the software you can use that doesn't require a continuous connection to the internet or doesn't access the internet without permission.
For example, Matthews iDSnet is an on-premises solution, which means the software and all data is stored on internal servers rather than all in the cloud. As a result, it doesn't need to be online and sits behind your firewalls and other levels of cyber protection.
This is because it has a perpetual licence, which means paying for it upfront and having the right to use the software indefinitely. Unlike subscription licences, the software does not need to connect to the internet and do regular checks to see if your licence is still valid and to perform updates.
You can still safely connect to the internet when needed – such as when you need remote support – thanks to appropriate and up-to-date security measures that secure the connections.
If you do prefer cloud software, the key is to look for a solution that puts you in control. For example, iDSnet Cloud prompts you when connecting to the internet to check you want to give it access.
In addition, Printernet is an element of the Matthews’ Care 24x7 offering; this cloud-enabled technology allows the Matthews technical support team to remotely access a coding device to check, diagnose and monitor its condition. This can be done securely on a parallel network or isolated network so not to put the rest of the infrastructure at risk.
Also consider the security of the device, including what the manufacturer has built into the product, and how and what information is stored and transferred. What servers do they use? Do they have a cyber audit program?
Make sure your software and hardware have clearly defined user permissions, password policies, multi-factor authentication and antivirus software. If not, you are leaving your network of IIoT devices vulnerable to attack.
Hardware and software should not be left open or exposed to unauthorised access. Remember, not everyone in the business needs access to everything, all the time. So, employ strict access controls where access is granted only to those with the proper credentials.
For example, with Matthews iDSnet, you can have as many users and passwords as you need. Users can be set up as an operator, supervisor or maintenance, and you can control the level of data and functionalities they can access; for example, you might choose only to let a user edit the database and access the label designer.
Take a “zero trust” approach, which requires a mindset based on three key principles: assume nothing, check everything, and limit access.
How do your systems talk to each other? It only takes one weak link to bring the whole system down, so if one system is compromised during a software update, any system it talks to is also vulnerable.
Some systems are designed to mitigate this risk.
With Matthews iDSnet, communication with other systems is via “neutral” or “common” locations, such as accessing data through SQL tables, .csv files stored in a common location, or connecting to other systems via a Web API. By communicating this way, rather than talking directly to other software packages, it means Matthews iDSnet prevents risk around other system changes and updates causing issues with iDSnet.
This open architecture means that many sources internally can integrate the data. A manufacturer might well have multiple different sources of data, including:
Because iDSnet is agnostic and utilises the common ground, if you choose to change ERP or warehouse management system, this will generally not affect the system.
Upgrading your software to more secure solutions is a critical way to protect your systems.
Attackers can more easily exploit existing vulnerabilities if you have operating systems that haven't been updated with the latest security. One survey revealed that while one in five organisations said they apply updates daily, and a third said they apply them weekly, almost a quarter only apply security updates once a month. In addition, organisations are worse at applying updates when they need to be done manually.

Human error, such as clicking a link in a phishing scam, is a huge threat to cybersecurity. According to the Fortinet study, 42% of respondents experienced insider breaches in 2021, up from 18% the previous year.
It is vital to educate employees on security protocols and keep them informed of any risks and changes.
Focus on ensuring the resilience of Industry 4.0 systems by creating a business continuity and disaster recovery plan, including backups and cybersecurity testing.
Test the plans periodically and adapt them according to lessons learnt from tests and actual security incidents.
When it comes to cybersecurity, manufacturers cannot afford to wait. So bolster your cybersecurity and safeguard your production line now – not when it's already too late to protect against potentially damaging attacks.